一、安装Nginx和OpenSSL
- yum install nginx openssl -y
二、SSL 服务器 / 客户端双向验证证书的生成
- 创建一个新的 CA 根证书,在 nginx 安装目录下新建 ca 文件夹,进入 ca,创建几个子文件夹
mkdir ca && cd ca
mkdir newcerts private conf server
# newcerts 子目录将用于存放 CA 签署过的数字证书(证书备份目录);private 用于存放 CA 的私钥;conf 目录用于存放一些简化参数用的配置文件;server 存放服务器证书文件。
- conf 目录新建 openssl.conf 文件
[ ca ]
default_ca = foo # The default ca section
[ foo ]
dir = ./ # top dir
database = ./index.txt # index file.
new_certs_dir = ./newcerts # new certs dir
certificate = ./private/ca.crt # The CA cert
serial = ./serial # serial no file
private_key = ./private/ca.key # CA private key
RANDFILE = ./private/.rand # random number file
default_days = 365 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = sha1 # message digest method to use
unique_subject = no # Set to 'no' to allow creation of
# several ctificates with same subject.
policy = policy_any # default policy
[ policy_any ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = match
localityName = optional
commonName = supplied
emailAddress = optional
- 生成私钥 key 文件
openssl genrsa -out private/ca.key 2048
输出
Generating RSA private key, 2048 bit long modulus
.......+++
.........................+++
e is 65537 (0x10001)
private 目录下有 ca.key 文件生成。
- 生成证书请求 csr 文件
openssl req -new -key private/ca.key -out private/ca.csr
- 生成凭证 crt 文件
openssl x509 -req -days 365 -in private/ca.csr -signkey private/ca.key -out private/ca.crt
private 目录下有 ca.crt 文件生成。
- 为我们的 key 设置起始序列号和创建 CA 键库
echo FACE > serial
#可以是任意四个字符
touch index.txt
- 为 "用户证书" 的移除创建一个证书撤销列表
openssl ca -gencrl -out ./private/ca.crl -crldays 7 -config "./conf/openssl.conf"
# 输出
Using configuration from ./conf/openssl.conf
private 目录下有 ca.crl 文件生成。
三、服务器证书的生成
- 创建一个 key
openssl genrsa -out server/server.key 2048
- 为我们的 key 创建一个证书签名请求 csr 文件
openssl req -new -key server/server.key -out server/server.csr
- 使用我们私有的 CA key 为刚才的 key 签名
openssl ca -in server/server.csr -cert private/ca.crt -keyfile private/ca.key -out server/server.crt -config "./conf/openssl.conf"
# 输出
Using configuration from ./conf/openssl.conf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :ASN.1 12:'GuangDong'
localityName :ASN.1 12:'GuangZhou'
organizationName :ASN.1 12:'le****'
organizationalUnitName:ASN.1 12:'dev'
commonName :ASN.1 12:'le***'
emailAddress :IA5STRING:'****@gmail.com'
Certificate is to be certified until Mar 19 07:37:02 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
注:签名信息每次必须输入一致
四、客户端证书的生成 * 创建存放 key 的目录 users
mkdir users
* 为用户创建一个 key
openssl genrsa -des3 -out ./users/client.key 2048
输出:
Enter pass phrase for ./users/client.key:123
Verifying - Enter pass phrase for ./users/client.key:123
#要求输入 pass phrase,这个是当前 key 的口令,以防止本密钥泄漏后被人盗用。两次输入同一个密码(比如我这里输入 123),users 目录下有 client.key 文件生成。
- 为 key 创建一个证书签名请求 csr 文件
openssl req -new -key ./users/client.key -out ./users/client.csr
#users 目录下有 client.csr 文件生成。
- 使用我们私有的 CA key 为刚才的 key 签名
openssl ca -in ./users/client.csr -cert ./private/ca.crt -keyfile ./private/ca.key -out ./users/client.crt -config "./conf/openssl.conf"
- 将证书转换为大多数浏览器都能识别的 PKCS12 文件
openssl pkcs12 -export -clcerts -in ./users/client.crt -inkey ./users/client.key -out ./users/client.p12
输出
Enter pass phrase for ./users/client.key:
Enter Export Password:
Verifying - Enter Export Password:
输入密码后,users 目录下有 client.p12 文件生成。
五、Nginx配置
- vhosts.xxx.conf 在 server { }段国入如下代码
listen 443;
server_name localhost;
ssi on;
ssi_silent_errors on;
ssi_types text/shtml;
ssl on;
ssl_certificate /usr/local/nginx/ca/server/server.crt;
ssl_certificate_key /usr/local/nginx/ca/server/server.key;
ssl_client_certificate /usr/local/nginx/ca/private/ca.crt;
ssl_session_timeout 5m;
ssl_verify_client on; #开户客户端证书验证
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDH:AES:HIGH:!aNULL:!MD5:!ADH:!DH;
ssl_prefer_server_ciphers on;
- 重新启动Nginx
六、客户端访问验证
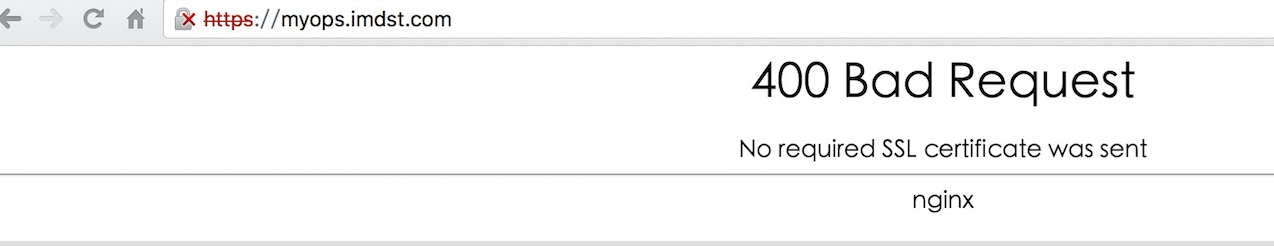 * 这是因为 https 双向验证需要客户端安装证书。拿到生成的客户端证书 client.p12,直接双击它,进入 "证书导入向导":
* 这是因为 https 双向验证需要客户端安装证书。拿到生成的客户端证书 client.p12,直接双击它,进入 "证书导入向导":
导入证书,直接双击下一步,下一步,输入密码,下一步,导入完成。重新打开浏览器测试
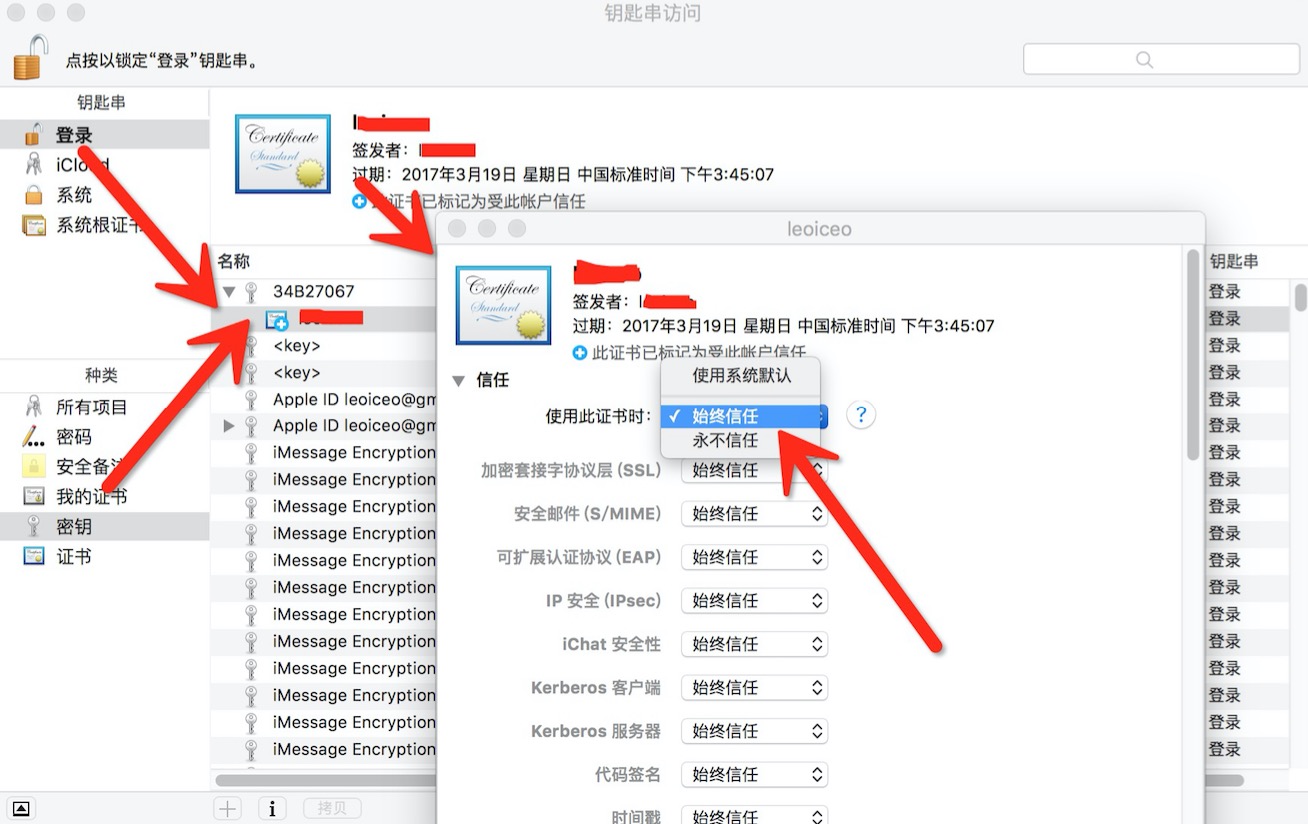
- MAC下需要手动添加为信任钥匙串,并使用safari打开测试
 Linux运维笔记|自动化运维攻城狮
Linux运维笔记|自动化运维攻城狮